We are strongly committed to protecting the privacy of your personal information.
This privacy policy is for this website [JustChant.co, CeaselessFlowOfDaimoku.com, CeaselessFlowOfDiamoku.com]
and served by CFOD and governs the privacy of its users who choose to use it.
The policy sets out the different areas where user privacy is concerned and outlines the obligations & requirements of the users, the website and website owners. Furthermore the way this website processes, stores and protects user data and information will also be detailed within this policy.
By accessing this site, certain information about the Reader, such as Internet protocol (IP) addresses, navigation through the Site, the software used and the time spent, along with any other information available to the Webmaster of the Site, will be stored on the CFOD servers. These will not specifically identify the Reader. The information will be used internally only for website maintenance purposes and traffic and statistical analysis. If the Reader voluntarily provides unique identifying information, such as name, address and other information on forms stored on this Site, such information will be used only to the extent expressly agreed by the Reader for originally intended purposes of use and will not be published for any other purpose unless otherwise specified.
The CFOD, however, assumes no responsibility for the security of this information.
We also use cookies see our Cookies Policy for more details [...]
 Open Authentication is a password-less authentication
system where your password is held else with Facebook or
Google etc, this we'll offer users a richer experience through
their social profile and personalized information. Passwordless
connections allow users to login without the need to remember
a password. Breached password detection protects and notifies
users when their credentials are leaked by a data breach
of a third party (Facebook or Google etc).
Access my be prevented until you have reinsert your password on the third party system.
Open Authentication is a password-less authentication
system where your password is held else with Facebook or
Google etc, this we'll offer users a richer experience through
their social profile and personalized information. Passwordless
connections allow users to login without the need to remember
a password. Breached password detection protects and notifies
users when their credentials are leaked by a data breach
of a third party (Facebook or Google etc).
Access my be prevented until you have reinsert your password on the third party system.
New sign-in detection
We take security very seriously and we want to keep you in the loop on important actions in your account.
If you use Google or Facebook to sign of to the site, this means that this site does not hold your password, or any data that could be breached if the ste was every hacked.
Many sites are hacked, from Facebook to Yahoo. The additional benefit of using Google or Microsoft to Authenticate who you are,
is that you will get an emails telling you that your identity has been used on a new device, such as a smart phone or computer.
Why would it ask for my location?
The app will now and again ask for your location from amy source it can find, this is so your Daimoku is recorded in your location, the correct country and nearest city.
We make an estimated location inferred from your IP address, which means we can guess that "Brighton and Hove, United Kingdom" is your usual location,
but if 5mins later you also login from "Beijing, China" then you have been hacked and you might want to know about it.
Facebook
Because Facebook do not care if you have been hacked (its your fault).
In April 2021, a large data set of over 509 million Facebook users was made freely available for download.
Encompassing approximately 20% of Facebook's subscribers, the data was obtained by exploiting a vulnerability Facebook advises
they rectified in August 2019. The primary value of the data is the association of
phone numbers to identities; whilst each record included phone, only 2.5 million contained an email address.
Most records contained names and genders with many also including dates of birth, location, relationship status and employer.
Which means, shortly after your account has been hi-jacked, data raped, then a day later you get locked out of facebook because 'you' have breached their community standards - and you did not even know about it.
Your Password has changed
If you have chosen password authentication method with us, when it changes you will be notified by email.
Ideally we would prefer not to have your username and password as there is no way it can be breached if it does not exist.
But on the other hand people like Profile and like to personalize their experience - like you cant say you belong to a given district if you are nobody.
- Has your email been 'breached', that is your LOGIN DETAILS have been leaked one or more times to hackers.
Check your email address to see if it been hacked.
- Has your password been 'breached', that is your LOGIN DETAILS have been leaked one or more times to hackers.
Pwned Passwords are hundreds of millions of real world passwords previously exposed in data breaches. This exposure makes them unsuitable for ongoing use as they're at much greater risk of being used to take over other accounts. They're searchable online below as well as being downloadable for use in other online systems
Create a strong password for your account
An 8 character passwords can be cracked in 4 days using a freely download-able password cracking tool from the Internet.
Just adding 2 more characters to your password extends that to 4 years for a 10 character password. You could just add the year (eg 17) or month and year (eg aug17)
to some part of your usual password to add security.
You can add further security by adding language specific special characters and whilst the USD symbol ($) is as old as the internet others requires a keyboard for that region (eg GBP £),
the restriction can be try logging in from a different country and not being able to find the cent (¢) symbol on your input device.
Password are usually case sensitive, so it is usual just to use an uppercase for the start of a new word, and have a mixture of numbers and common symbols.
If a password is so complex you cannot remember it and so have to write it down, then that is a problem, you could use the first letter of each word in a sentence, and maintain the difference with a year and month number.
You could also use an app such as LastPass that stores all your passwords and uses biometric protection to use the password.
It is especially important to have a strong password if you use a Microsoft email address (like Outlook.com or Hotmail).
This is because many services now use your email address to check your identity. If someone gets access to your Microsoft account, they may be able to use your email to reset the passwords for your other accounts, like banking and on-line shopping.
In addition you may wish to Reset your password as well. If you notice that you are getting a lot of fake spam emails you may want to see if your emails
has been breached elsewhere.
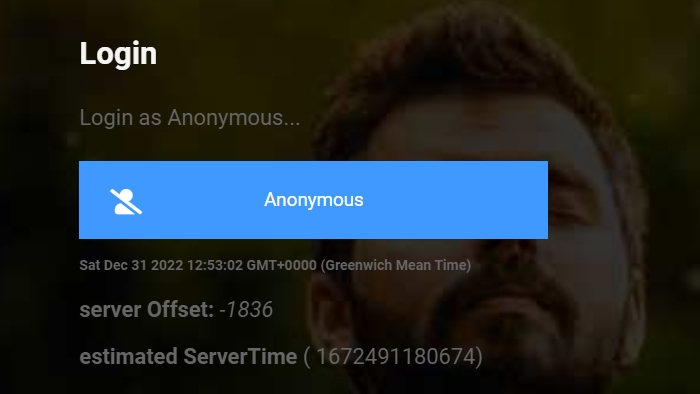
Anonymous User
So as a user you can login Anonymously and you dont have a profile.
Your device is uniquely identified, if you log out and back in again you are a different person
- all we need to know is when you start and stop chanting - that's it.
The time code GMT+0000 (Greenwich Mean Time) just tells you the time on the server.
Anonymous Tracking
Your device is uniquely identified, so its your mobile phone that is chanting in a given timezone, not a person.
You could log in from an internet cafe and claim to be chanting.

Anonymous Profile
If you log in as Anonymous, and register your device, is you log out again and then back in again on that same device then you will be remembered.
The only difference is that if it was a 'Desktop' it could be in a cyber-cafe if it was a 'Mobile Browser' then its likely to be a mobile phone.
In Version 1.0 of this app we will go for Anonymous first.
Passwordless and two factor Authentication
Google or Microsoft Two Factor Authentication requires that you supply more that one proof of identity, this might be an SMS text message to a trusted phone or a code to a pre-authenticated app on your smart phone and you enter that code as well as your password.
Since there is a cost involved in sending SMS Text messages this would be limited to paid accounts.
Passwordless - is taken to mean that you have already authenticated to Facebook or Twitter so we would trust that as a logon method. The more choices of how you can logon add to the cost, see Paying the Rent for more details.
Some mobiles use a finger print to log-in or 'my voice is my password' biometrics - this way we never see your password as we used a trusted third party such as google or facebook or twitter to authenticate.
If you have not manually logged off please check that the email you use here has not been breached elsewhere.
If your email or identity has been breached - change your password and security questions.
We take security and privacy seriously this is why we offer 'Password-less' logon methods (there is no data to breach).
You can check if you have an account that has been compromised in any data breach via the data below:
Has your email and Password been sold on the Dark Web?
Data Breaches are where some system has been hacked
and some part of your personal data has leaked from a safe place into the wrong hands, data such as Email addresses, IP addresses, Names, Passwords, Phone numbers, Physical addresses, Usernames etc.
The haveibeenpwned site check in the email you use to logon has been abused and inso ware.
Which means it mak not be you that is logging into this site at all.
Copyrights
Readers shall not use this Site or any information thereon in violation of any rights provided by any law, policy, rule or regulation of any country and region or for any illegal activity or any activity prohibited by any law, policy, rule or regulation of any country and region.
The CFOD is not responsible for such illegal use of the copyrighted Materials.
Technology
This site uses cookies from Google to deliver its services and to analyse traffic [...]
Your IP address and user agent are shared with CFOD, together with performance and security metrics, to ensure quality of service, generate usage statistics and to detect and address abuse.
Your user agent tells us amongst other things what language you may speak and what sized device you are using this allows us to help if you are using a slow mobile phone or a desktop computer.
Firewalls
Web Application Firewall is a cloud-native service that protects web apps from common web-hacking techniques such as SQL injection, security vulnerabilities such as cross-site scripting and other OWASP risks.
Deploy the service in minutes to get complete visibility into your environment and block malicious attacks.
If you dont use SQL then SQL cannot be injected.
But enhanced security costs money, like the cost of your website again, and if its free or just has
adverts then that wont cover the cost.
Paying the Rent
CSS & Theme
SINDEVO.COM - Smart Internet Development
Cookies Policy
We know your privacy is of the upmost importance and will take great care to ensure your information is managed securely and lawfully.
When personal information is collected through the website we will be upfront about how we will use it and why it needs to be collected.
When you visit this website, cookies are used to collect anonymous information so that your user experience can be improved in the future.
What are cookies?
Cookies are small text files saved to your website browser that help us identify who you are. We use cookies for several reasons. Essential cookies are required to drive the authentication process, so you dont need to keep logging in all the time - do it once and forget. Non-essential cookies are used to optimise the look and feel of the site, providing feedback on site usage.
More about Cookies[...]
What types of cookies do we use?
We use session, persistent and third-party cookies on our websites. Session cookies exist for the duration of a visit and are erased when you close the web browser. Persistent cookies are stored until they expire, which can range from several minutes to many years. Third-party cookies are provided by our trusted partners and are either session or persistent.
Accepting or rejecting cookies
You may be able to adjust your internet browser to warn you when a new cookie is about to be stored, that way you can make a decision whether to accept or reject it. If cookies are already on your system, you can delete them.
The Cookies we use are explained below
-
Google Analytics
We use Google Analytics cookies to give us insights into our website traffic and marketing effectiveness. It helps us optimise and target our activities more effectively. Again, all your data is anonymised.
About Google Analytics Cookies[...]
-
Hotjar
We use Hotjar to provide us with more in-depth data on the behaviour of users on our site. In other analytics tools, we can just see the number of people doing certain things. Hotjar allows us to answer questions about why users are doing these things. E.g. we can see the page elements over which our users hover most often, we can see the exact form fields people have trouble completing and we can actually re-play the entire visit of certain users. This helps us to find and fix all the little bugs and problem areas of our site. Any sensitive user information is not visible to us and personal data is not stored.
About Hotjar Cookies[...]
-
Double Click
We use Google’s DoubleClick products to manage and optimise our paid online advertising.
The cookies used by DoubleClick essentially just tell us whether or not you’ve either seen or clicked on one of our ads. If you’ve already clicked on one of our Ads for example, we might not want you to see any others for while. So this simple cookie data just allows us to improve our ad performance and make our ad targeting more accurate.
No personal information is stored and all behavioral data is anonymised.
About Double Click Cookies[...]
-
Termly
"Termly is your all-in-one compliance solution for complex data privacy laws worldwide. Privacy policy generators, cookie consent, and more."
About Termly [...]
TODO --------------------------------------
GDPR
TODO.
Add GDPR module for data request and clean up, copy what I do at work.
Disclaimers
There are many Buddhists that chant nam(u) myoho renge kyo.
I belong to one, yet I have friends in others. This site aims to bring together what unites us rather than what divides us.
Therefore there are links to all the traditions including my own.
SGI Orthodoxy
As if the Priesthood issues was not bad enough there is the internal not invested here issues,
and if we did not like all the occult rituals of one group, yet others are ok.
All that matters is that we chant nam myoho renge kyo and make a difference where we can through the power of the practice.
Materials provided on this Site are provided "as is," without warranty of any kind, either express or implied, including and without limitation, warranties of merchantability, fitness for a particular purpose and non-infringement. The CFOD specifically does not make any warranties or representations as to the accuracy or completeness of any such Materials. The CFOD periodically adds, changes, improves or updates the Materials on this Site without notice. Under no circumstances shall the CFOD be liable for any loss, damage, liability or expense incurred or suffered that is claimed to have resulted from the use of this Site, including and without limitation, any fault, error, omission, interruption or delay with respect thereto.
Neither the CFOD nor its affiliates, nor any of their respective agents, employees, information providers or content providers, shall be liable to any Reader or anyone else for any inaccuracy, error, omission, interruption, deletion, defect, alteration of or use of any content herein, or for its timeliness or completeness, nor shall they be liable for any failure of performance, computer virus or communication line failure, regardless of cause, or for any damages resulting therefrom.
As a condition of use of this Site, the Reader agrees to indemnify the CFOD and its affiliates from and against any and all actions, claims, losses, damages, liabilities and expenses (including reasonable attorneys' fees) arising out of the Reader's use of this Site, including and without limitation, any claims alleging facts that if true would constitute a breach by the Reader of these Terms and Conditions. If the Reader is dissatisfied with any part or parts of the Materials on this Site or with any of its Terms and Conditions of Use, the Reader's sole and exclusive remedy is to discontinue using the Site.
This Site may contain links and references to third-party websites.
The linked sites are not under the control of the CFOD, and the CFOD is not responsible for the content of any linked site, any link contained in a linked site or the privacy policy of any linked site.
The CFOD provides these links only as a convenience, and the inclusion of a link or reference does not imply the endorsement of the linked site by the CFOD.
CFOD and this site is not affiliated to SGI
Dedications, Appreciation and Thanks